A Comprehensive Guide to Internet Privacy Tools and Techniques
Privacy tools are software apps that empower you to exert more control over what information is shared about you, publicly and commercially.
Whether you are on the internet for advertisement purposes, product recommendations or even to solve serious crimes, the information about you is always collected. These are crucial and they require having online privacy and protecting your data whenever you are surrounded by the internet so that you do not become a victim of cyber-crime. Ensuring your privacy in life also saves you a lot of struggles.
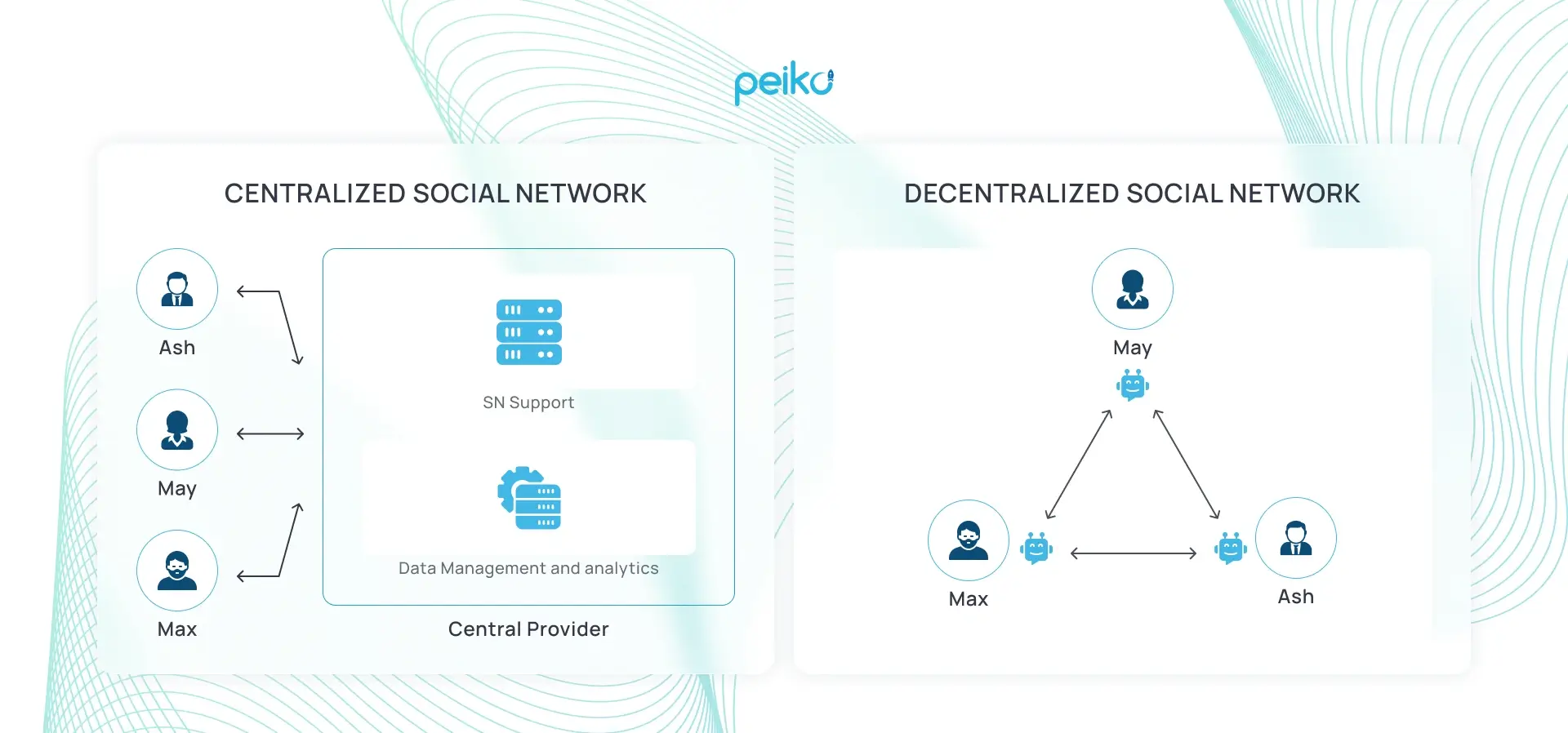
Web browsers
Web browsers are programs that allow users to enter the World Wide Web, the most valuable virtual collection of human knowledge ever created, just one-click away. Secondly, they are tools that can safeguard the privacy of users by monitoring what information they receive from cyberspace.
Also most browsers provide in browser privacy options such as private browsing, clearing logs and deleting cookies, interface arrangement such as language and layouts and favourites/bookmarks for common use along with extensions for additional functionality.
There are privacy options available on all of the major four browsers, although the way each browser works is just a little different. Setting up online privacy works differently depending on whether you are on a Mac or a PC; check out our Tech Safe Survivor Resources Toolkit for more tips on tech safety for survivors! Keep your browsers updated as well, and private window mode, always!
VPNs
VPNs (virtual private networks) encrypt internet traffic, making it more secure for the user. This prevents your ISP from knowing what you are browsing. It also protects your privacy better than features found within web browsers such as incognito mode.
Hides your IP address so sites and services don’t use your location to block content you’re trying to access – useful for anyone travelling, for example, or simply working remotely and wanting to access the content that would normally be blocked or inaccessible in your home country.
VPNs can also serve as a protective measure against hacks, safeguarding your identity by keeping your browsing habits private and making it more difficult for identity thieves and other bad actors to succeed. Of course, strong passwords and avoidance of malicious-looking websites or downloads are still good practices. A corollary to passwords (though less simple) is that VPNs do not protect against viruses. These malware infections prey on software bugs and might still get foot holds through social engineering or email phishing and ads.
Password managers
Digital security guards, in the form of password managers, grant busy users the ability to marshal all of their website, app and program logins into a single, secure depository, auto populating them only when needed, thus performing those logins in the background as needed.
The best password managers protect your data with advanced encryption; even if cybercriminals get access to it, they will be met with only scrambled data – not your login info!
Other features you might want in a password manager include two-factor authentication; password generation; and secure sharing between all your devices – not to mention secondarily watching dark-web or data-breach sites in case your account is poking around there so you can change passwords before the bad guys do.
Private browsing mode
All major web browsers have private browsing modes – my Safari browser calls it incognito mode – which hide what you search for or read wherever you go. I use it, for example, when I want to log into multiple email accounts with one computer. If you shop online or research something touchy, like whether your love bite is normal or something more alarming, you can use private browsing to avoid having your browsing history broadcast to everyone else who has ever used the same computer.
do not think this ‘privacy mode’ will stop all tracking or hacking. For example: employers could still track you, if you are using devices belonging to them; and advertising companies could still track you online to serve you with adverts; and your information could still be hacked through entry by spyware.
While these features can be helpful, they should not be your only source of protection. To learn more about technology resources, see Safety Net’s Tech & Survivor Resources Toolkit.
MetaGer
Internet privacy involves the right to protect personal information while browsing the web. This can be achieved with the use tools such as VPNs, password manager or private search engines, which help to avoid tracking by hackers and companies. Moreover, internet privacy also protects the freedom of speech and expression of people during their communication.
MetaGer is a metasearch engine – which, as the name suggests, searches through multiple different search engines, presenting the best possible results from each query. Unlike Google, searches do not involve having a machine calculate what you think will interest you, only by analysing what previously interested you Beyond explicitly selecting an engine that prioritises privacy, the reason I recommend this site is that all of its servers are based within Germany. The reason I say this is important is that German privacy law tends to prioritise privacy over other nations in Europe.
Among its other special features is a meta-search, with the option to go to Google, special image searches and sophisticated content-search features accessible through the search icon in the top left corner. Tor is available for a secure connection.